

Published il y a 1 mois
Hi, This is DevSecure Team
,we specialize in uncovering hidden vulnerabilities that pose real-world risks to modern web applications.
All vulnerabilities shared in these write-ups are fully redacted — any company names, domains, or sensitive details are replaced with placeholders such as company.com. Each finding was responsibly disclosed through the Intigriti platform and has been verified and resolved by the affected vendor.
Every post represents our commitment to ethical hacking, responsible disclosure, and continuous learning, helping organizations strengthen their defenses while contributing to a safer global cybersecurity ecosystem.
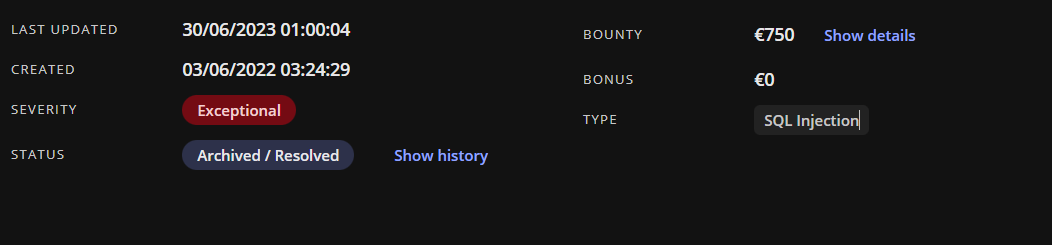
service-xx.company.com, there was some similare website service-aa.company.com, service-bb.company.com,service-cc.company.com all similare, but this one service-xx.company.com it has some special behavior whene i access to service-xx.company.com/app i got 302 redirect to login page, not like the other services has 404 not found error. from there i know thats it has to be somthing hosted for there internal team. after some recon i found a regetration page in http://service-xx.company.com/ i bypass thats and loged in by create new account evene im not autorized (misconfiguration) https://service-xx.company.com/app/basic/xxxx/create_accountthan i loged in as one of there internal staff, in this support admin webapp i found an interesting sql injuctionAffected Parameter / Endpoint: - https://service-xx.company.com/app/searchResults
https://service-xx.company.com/app/basic/xxxx/create_account POST /app/searchResults HTTP/1.1 Host: service-xx.company.com Cookie: xxx Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: https://service-xx.company.com/app/xxxx Accept-Encoding: gzip, deflate Accept-Language: fr-FR,fr;q=0.9,en-US;q=0.8,en;q=0.7 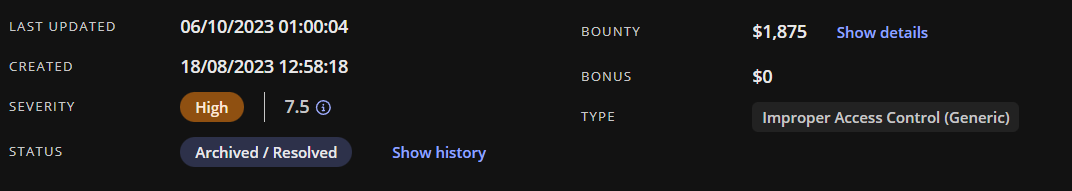
Description: BROKEN ACCESS CONTROL lead to leak all users sensitive data in company database, including emails in compa...
Read More →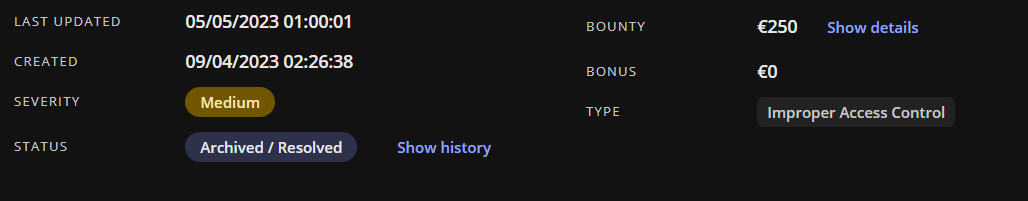
Description: Broken access control IDOR lead to get all invoices for any customer Affected Parameter / Endpoint: https...
Read More →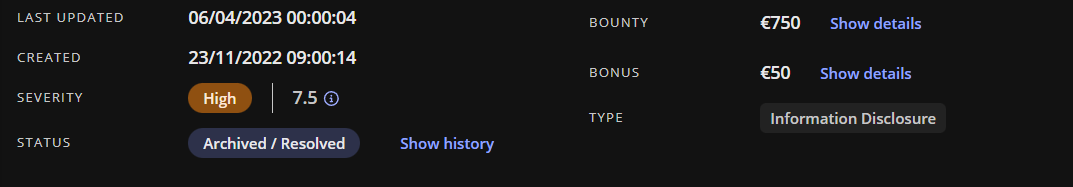
Description: i found a vulnerability thats make me able to extract all employees documents thats has sensitive informat...
Read More →