

Published il y a 3 mois
Hi, This is DevSecure Team
,we specialize in uncovering hidden vulnerabilities that pose real-world risks to modern web applications.
All vulnerabilities shared in these write-ups are fully redacted — any company names, domains, or sensitive details are replaced with placeholders such as company.com. Each finding was responsibly disclosed through the Intigriti platform and has been verified and resolved by the affected vendor.
Every post represents our commitment to ethical hacking, responsible disclosure, and continuous learning, helping organizations strengthen their defenses while contributing to a safer global cybersecurity ecosystem.
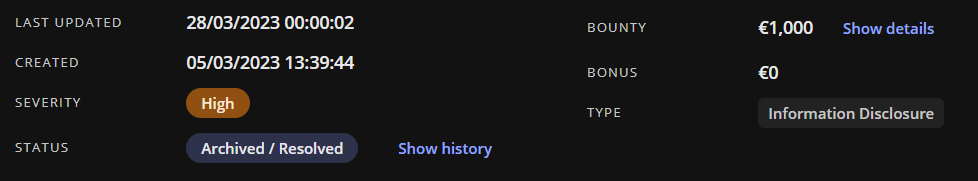
1/ create new company and login 2/ go to services-api.company.com/customers/{UUID}/invoices?invoiced=false 3/ change UUI...
Read More →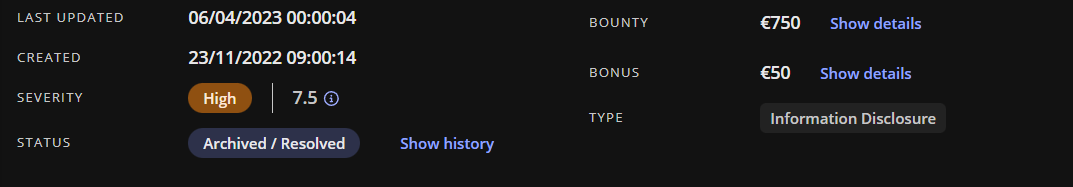
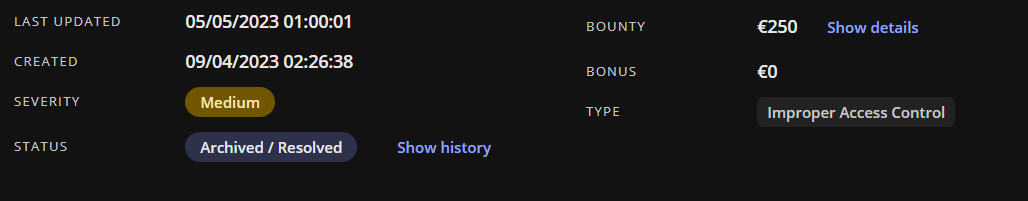
1/ go to this endpoint https://company.com/search?p_p_lifecycle=0&saveLastPath=true&q=cv&type=com.liferay.document.libra...
Read More →
Export Support Company Search Subscription Application Instance List and Support Company Search Customers Tunnels List...
Read More →